Invisible to standard internet browsers and search engines, the Dark Web is a place where users anonymously access content which is either illegal or related to illegal activities. This includes the lucrative marketplace for stolen login details, which are bought by criminals who are able to monetize the data and permissions they unlock. Among these, your Nfield login is a desirable prize, as it opens the door to a large pool of personal information.
How desirable? This can be worked out by taking a look at trading prices for the items your Nfield data helps unlock.
Dark Web Price Index
The illustration below shows the process a hacker would go through to harvest your survey participants’ login details from Nfield and make them saleable. If we work backwards from the end prize, we get an idea of the financial temptation.
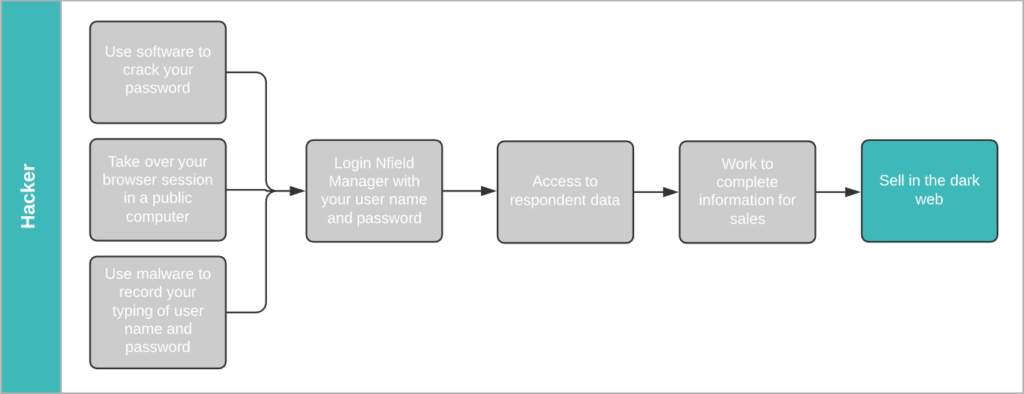
According to Dark Web Price Index 2020, a stolen Gmail login (email address/username + password) sells for $155.73. A hacker who obtains your Nfield Manager login name and password gains access to all the sample information in all your surveys. That’s likely to include a high percentage of valid Gmail addresses. To make these saleable on the dark web, all the hacker now has to do is get the corresponding passwords.
Stealing passwords
Hackers commonly obtain passwords via phishing emails and database matching. Both of which are automated processes that easily deliver the goods.
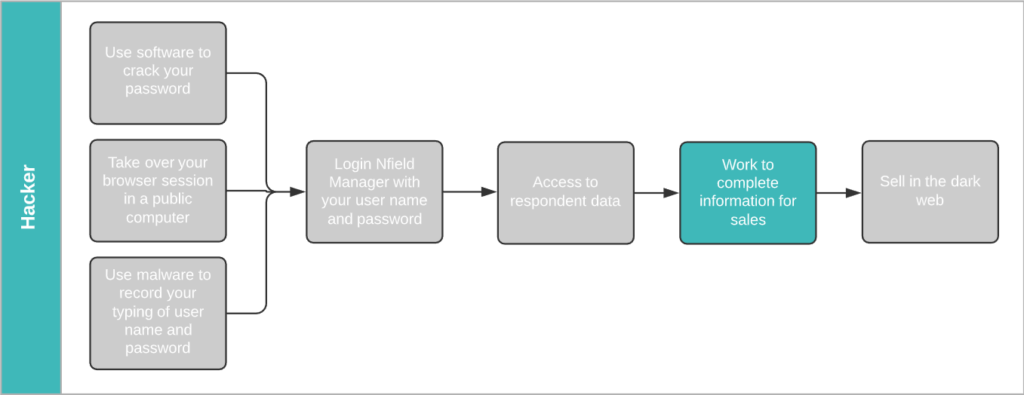
Phishing Emails
Because login to Google accounts is protected by limitation on incorrect password attempts, there’s no point in trying to obtain passwords by endless guessing. Phishing, whereby a hacker approaches you via fake emails pretending to be from a trusted source and asks you to sign in to a related account – thereby revealing your password – is a far more successful method.
Every successful attempt can reap multiple payouts for the hacker. According to LastPass, 65% of people re-use passwords. A lucky hacker could net themselves an additional $74.50 if the same login details give access to a Facebook account and $50 each for Twitter and Instagram accounts1.
Database matching
Another popular commodity traded on the dark web is credit card details, which sell for between $12 and $20 each.

Credit card details are composed of two parts. The first part is the info displayed on the card itself – credit card number, expiry date, CVV number (on the back) and holder name. These are plentifully available in a nicely formatted database, obtained through skimming devices planted in ATM machines, train ticket machines and are even sold by unscrupulous retailers who’ve been paid via card swipe machines.
The second part is the card owner zip code (derived from address), city, address, email and phone. Details which are commonly held in survey sample data! Armed with this information, a hacker can easily run a database matching tool between a purchased credit card database and your sample data to obtain complete sets of credit card details, ready to sell.
If you think this seems a lot of work for relatively modest returns, think again. Phishing and database matching are automated processes which take no more effort than a few clicks. Easy money.
How your Nfield account could get hacked
Hackers have all the tools they need to crack your password, take over your browser session and use malware to get hold of your Nfield login.
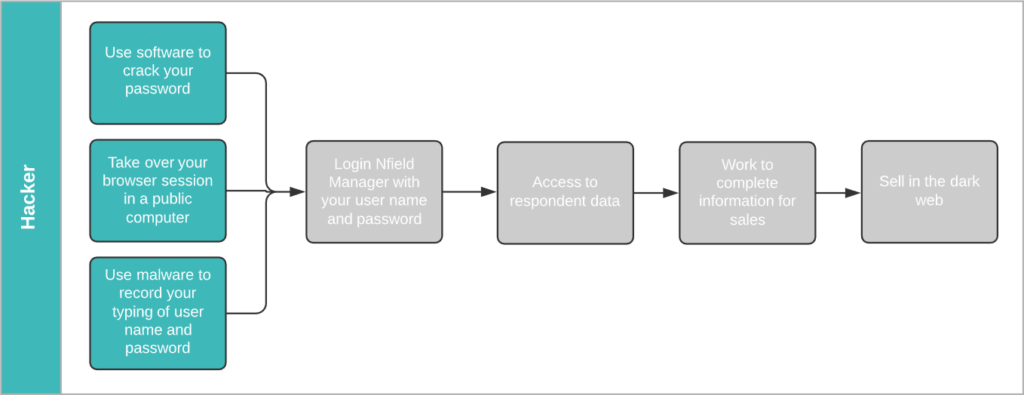
Cracking passwords using software is a basic skill in the hacking world. It’s simply a matter of time. Did you know 90% of passwords can be cracked in less than six hours2.
Using shared computers in public spaces, such as cafés, airport lounges or even client meeting rooms, can lay out the welcome mat for hackers. You never know who’s hanging around waiting to inspect your activity in the event of you rushing off without logging out, or through having installed password capture software.
At the time of writing, a great many of us are working from home due to the COVID-19 pandemic. In this situation, the companies we work for usually have very limited control over the equipment we’re using for both work and recreation. It’s a vulnerability that makes it easier to implant malware that records your key strokes and can hack into your Nfield account.
2 https://www.servalsystems.co.uk/6-facts-about-passwords-that-will-make-you-think/
Protect your gold mine
Although the sales values for individual login details and credit cards aren’t particularly high, they easily add up. How much do you think all the sample data held in your Nfield account is potentially worth to a criminal? Selling just one Gmail login per day would net a hacker over $56,000 a year. That’s too tempting to ignore. Which is why Nfield is now equipped with two-factor authentication, to keep hackers out of your account, even if they have cracked your password.

